PowerShell Network Inspector
Posted on June 23, 2025 by Ethan Fitzgerald
When tasked with examining a machine for possible compromise it can be sometimes be difficult to detect evidence of malicious activity. Wiping and imaging a machine is usually the best route as unless there is firmware level compromise this guarantees a safe resolution. However, this is not a time efficient solution and can minimize the effectiveness of defensive cyber operations. Thus a variety of tools are needed to thoroughly examine suspect machines and search for indicators of compromise (IOCs). In this article I will be showcasing a simple PowerShell script I created that can help detect evidence of malicious activity on a system. While many of my scripts are intended to be run remotely against a target list of machines to look for specific IOCs, this one is designed to be run on an ad hoc basis when a compromise is suspected, as it checks various threat intel sources in real time and reports status directly back to the console. It is not meant to replace traditional AV or EDR products, but to supplement their use in incident response. It is a quick, lightweight tool that gives immediate visibility into all the active TCP connections on a machine. I do plan on releasing a version in the future that doesn’t require user input and will log collected data to centralized storage, making it useful in large enterprise environments with hundreds to thousands of machines.
Network connection monitoring: this is the core of functionality of the script. In its most basic form, network connection monitoring is simply logging all connections being made to and from a device, or into or out of a network. This is useful in identifying malicious behaviors such as data exfiltration, DNS tunneling, beaconing, and command and control channels (C2). When an IP address is associated with malicious activities, it is often reported to centralized threat intelligence platforms to give the IT security community a reference point to check addresses against. These platforms frequently expose this data via an application programming interface (API), which allows us to programmatically interact with the data and integrate it into programs and scripts. Known bad IPs are oftentimes associated with specific threat actors, which can give us insight into what and who might be infecting systems on the network.
Usage: Upon launching the script, it will perform an initial collection of remote addresses. It does this using the Powershell cmdlet Get-NetTCPConnection. This command returns a list of current TCP connections, filters out the remote addresses, and then stores them in a nested hashtable for further usage.
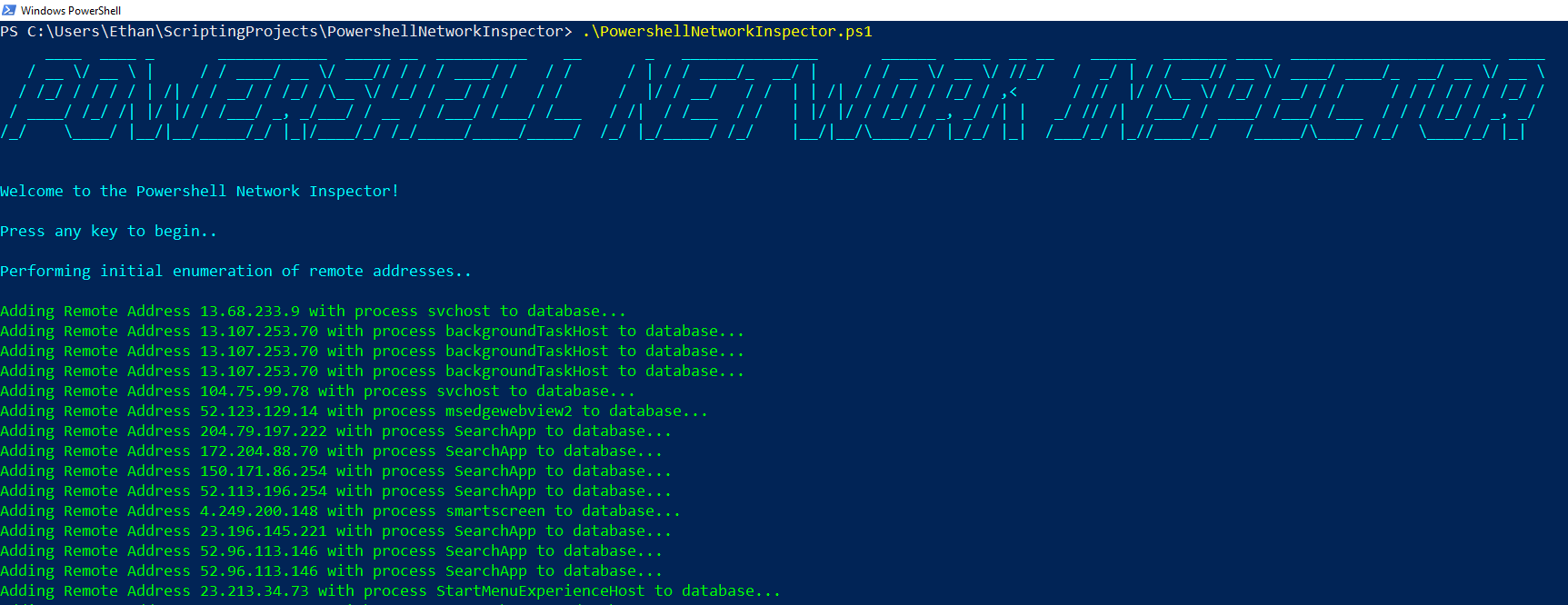
After the initial data collection has completed, the following commands are available:
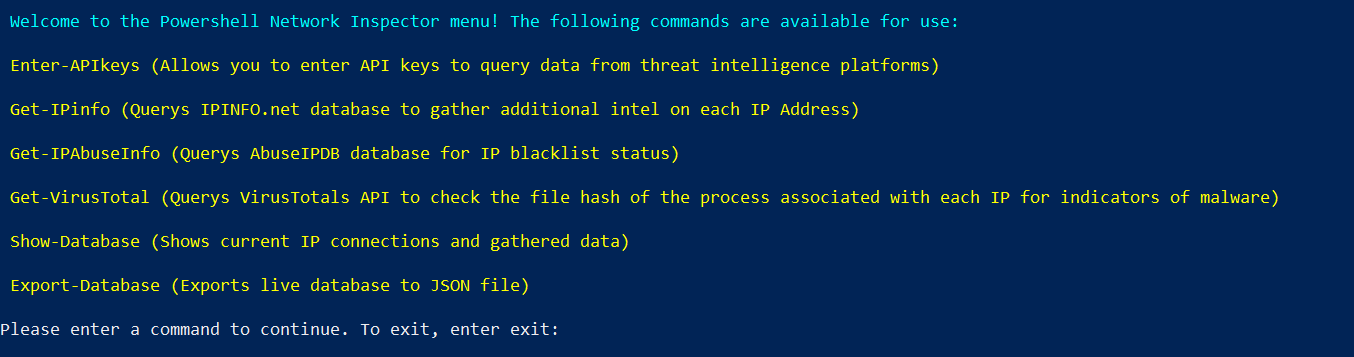
Enter-APIkeys: This option allows you to enter API keys, which are needed for full functionality. The script leverages three different threat intelligence platforms to collect data on each remote address, Virustotal.com, AbuseIPDB.com, and IPinfo.io. While the API keys are all free, an account is needed to create them. They keys can only be entered at runtime and are never stored anywhere on the disk.
Get-IPinfo: This option uses the Get-RestMethod cmdlet to check each remote address against IPinfo.io’s API. The following information is gathered for each address: hostname, organization, city, postal, GPS location, timezone, and region. While this information is not conclusive in determining whether a connection is malicious, it can be used to quickly screen for connections to suspicious regions of the world. Hint: if your system is connecting to somewhere like Albania, you are likely pwned.
Get-IPabuseInfo This option checks the AbuseIPDB database to see if each remote address has been reported for abuse. If an address has been reported for abuse with a confidence score greater than zero, the script will display the reported address highlighted in yellow and warn that it has been detected to be abusive. However, this does not necessarily mean that the system is compromised, further investigation is needed.
Get-VirusTotal: This doesn’t check any of the remote addresses, but rather a hash of the file associated with each running process responsible for each address. During the initial data collection of each network connection, the associated process is discovered, its filepath extracted, and a hash generated with the Get-FileHash cmdlet. This can cover gaps where AV is missing or has an outdated signature database. Virustotal restricts their free API to four requests per minute, so this can take some time as the script is rate limited to avoid exceeding the limit
Show-Database: This will list out all data to the console. While the script does not use a real database, it employs nested hashtables to structure and store the data. Good enough for one off scripts, but something like SQLite might be a better option for a version of the script designed to target multiple machines, as the data complexity would increase and nested hashtables would become cumbersome.
Export-Database: This command dumps the entire database into a json file in the current working directory.
While this script does not dive super deep into the network traffic, it is useful for a quick and dirty birds eye view of the network activity on a system. It should be used in conjunction with other tools such as Wireshark, Process Explorer, Autoruns, and malware scanners to positively identify infections. If you would like to use this script, it is available on my GitHub here: Powershell Network Inspector
← Back to Home